What is ransomware attack, how did it start and how to avoid it?

A malicious programme or ransomware has been used to deploy a massive cyber attack, infecting computers in nearly 100 countries.
Researches with security company Avast had observed 75,000 infections in 99 countries including Russia, Ukraine and Taiwan.
The ransomware has been identified a new variant of "WannaCry" that had the ability to automatically spread across large networks by exploiting a known bug in Microsoft's Windows operating system.
According to reports, the hack was deployed on Friday and forced British hospitals to turn away their patients. It also struck Spanish companies such as Telefonia, Portugal Telecom, the delivery company FedEx and a Swedish local authority. About 40 National Health Service (NHS) in England Scotland were hit by the attack.
-How it works-
Hackers tricked victims into opening the malicious malware attachment to spam mails that appeared to contain invoice, job offers, security warnings and other legitimate files.
The ransomware called WannaCry locks up files on computers and encrypts them in a way that it does not allow user to access them anymore.
It has been identified as an old variant of ransomware that exploited a known bug in Microsoft’s Windows operating system.
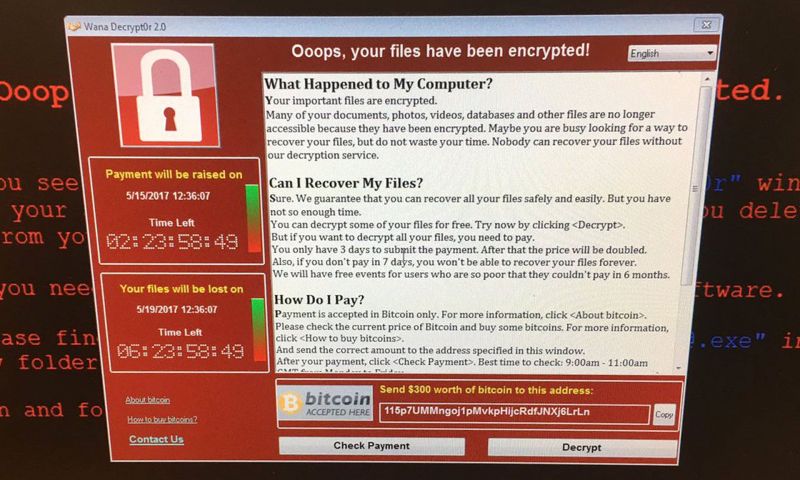
When an Windows operating system is affected by the malicious software, a pop-up window appears giving a detailed explanation on what has happened to your computer, how you can recover it and with instructions on how to pay a ransom amount of $300 in Bitcoin.
On the left, the pop-up window also features two countdown clocks, one showing a three-day deadline before the amount doubles to $600 and another showing a deadline when the victim will lose all his data.
-How did it spread-
Security researchers say in this case the infection seems to be deployed via a worm—a program that spreads by itself a network of computers rather than relying on humans to click on a spam mail or infected attachment.
Although the malicious program demands a ransom amount of money in order to regain access, experts warns there is no guarantee that the access would be granted after even making the payment.
-How to prevent the infection-
Microsoft on Friday said that it had added detection and protection against the new malicious software.
However, here is a list of measures that can be opted by Windows users as a precaution to protect themselves against the ransomware. The list is based on some steps provided by the Microsoft's Malware Protection Center.
- Install and use up-to-date antivirus solution such as Microsoft Security Essentials
- Avoid clicking on suspicious links or attachments or emails from unknown people or organisations.
- Install a pop-up blocker on your PCs
- Have smart screen turned on in Internet Explorer. It will help you identify reported phishing and malware websites.
- Create regular backup of your important files.
According to the reports, a cyber security researcher accidentally discovered a “kill switch” infused in the malicious program by hackers to disable the malware altogether in case they wanted to shut down their activities.
The 22-year-old researcher, who goes by the name of @MalwareTechBlog on Twitter, found the kill switch’s domain had not been registered. Taking advantage of the opportunity, he immediately purchased the domain himself for $10.69 and live the website, which helped him shut down the attack before it could fully reach the United States.